Cookies help us to deliver certain functionalities to you and to guarantee the best user experience possible. By continuing to browse and use this website you agree to our use of cookies in accordance with our Privacy Policy.
Cookies help us to deliver certain functionalities to you and to guarantee the best user experience possible. By continuing to browse and use this website you agree to our use of cookies in accordance with our Privacy Policy.
Enhanced Capabilities for Visibility up to L7
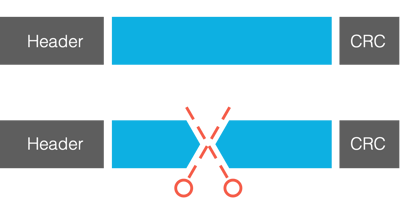
Packet Slicing reduces the volume of data to be forwarded for analysis and processing by a network appliance by reducing the packet length. This is especially useful for network applications that only require header analysis and or a defined set of bytes from each packet. Packet length is reduced based on user configurable rules.
Deduplication identifies and removes duplicate packets from being sent to a network appliance. While duplicate packets may occur on the network from backup and failovers deployment architectures, the more common occurrence is with the use of multiple SPAN ports across connected switches and routers that are feeding to a network appliance. When a network appliance handles duplicate packets, the duplicate packets consume the tools limited processing resources, resulting in significant performance degradation and may also affect the accuracy and results reported.
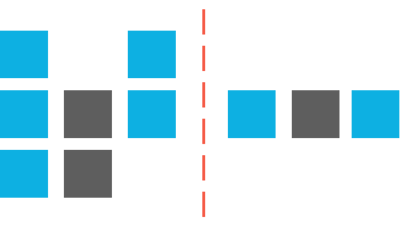
Figure depicts the function of deduplication. User can optimize deduplication for his network needs by configuring the window size and refining deduplication criteria based on header attributes.
With the increase in traffic capacity on the one hand and the need for greater processing granularity on the other, many network tools ingest traffic metadata rather than the raw traffic data packets themselves. There are well-standardized metadata frameworks as well as numerous specified fields and extensions for additional vendor-specific fields. Often, metadata reports are generated by the network element itself like a switch or a router. The disadvantage is that as metadata generation is not the primary objective of the switch or router, metadata performance generated by the switch or router may be degraded in times of congestion versus Niagara’s solution where such degradation does not take place. Furthermore, to address congestion, the switch or router utilizes traffic sampling, instead of taking into account every packet in the flow.
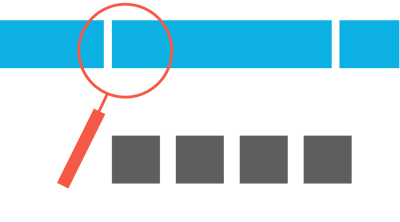
Figure depicts the function of Netflow generation. Netflow meta data is generated from the network traffic for the netflow/IPfix fields defined by the user.
Data Masking enables the enterprise to forward and share data traffic across departments, while at the same time providing them with a tool to mask private and confidential user information that is contained in the data.

Identification of applications and layer 7 protocols often require deep packet inspection and analysis. Application filtering performs DPI and supports the identification of dozens of applications. Supported application list is updated on a regular basis

SSL/TLS decryption offering is an important foundation of the security visibility layer. Without SSL/TLS Decryption your organization is blind to attacks, malware and other security and cyber threats impacting your network via the TLS layer. Organizations need a way to identify threats and malware in order to protect their users and intellectual property.
Niagara's SSL/TLS decryption platform supports three deployment modes:
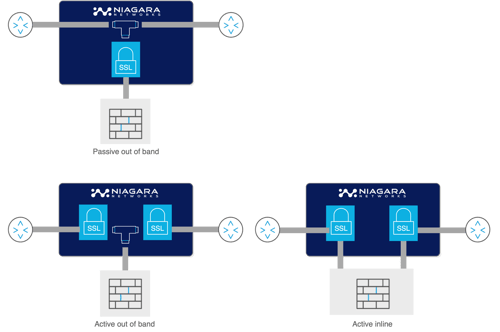
Figure depicts the three SSL/TLS network deployments. The three modes can bee support simultaneously on the same platform.
Tunnels are used to encapsulate traffic and send it from one location to another. This application supports the ability to encapsulate traffic and send it to a remote/central location. It also supports the ability to terminate a tunnels and forward the decapsulated (de-tunneled) traffic to a network tool

GTP Correlation encompases multiple applications associated with facilitating network tool connectivity in mobile environments. One of the primary challenges in mobile networks network tools, whether used for performance, monitoring, behavioral analysis, and or any other analysis that requires differentiating user traffic is that in mobile networks the user plane and control plane are decoupled. In order to correctly identify a specific user’s traffic we need to correlate it with the control/signaling plane. Other associated applications include optimized load balancing based on user traffic, IMSI filtering and more.
Header Stripping is designed to facilitate and modify traffic in a manner that the intended network tool can process it and fulfill its intended purpose. Niagara’s application will strip the header from the traffic exposing the relevant packet for processing
Regex Patterns application, functions as an expansion for existing filtering and data masking capabilities, while adding additional new modes of operation. The user can define any pattern through a regular expression, or load a predefined expression. With this capability, the user can perform advanced packet filtering, advanced masking and advanced session filtering. With session filtering, once the pattern is detected in any packet, the entire session is identified and can be filtered. For every pattern match, the user can configure to filter or to exclude the match.

© 2025 Niagara Networks. All Rights Reserved.